Data Loss Prevention
New DLP topic based detection entries for AI prompt protection
You now have access to a comprehensive suite of capabilities to secure your organization's use of generative AI. AI prompt protection introduces four key features that work together to provide deep visibility and granular control.
- Prompt Detection for AI Applications
DLP can now natively detect and inspect user prompts submitted to popular AI applications, including Google Gemini, ChatGPT, Claude, and Perplexity.
- Prompt Analysis and Topic Classification
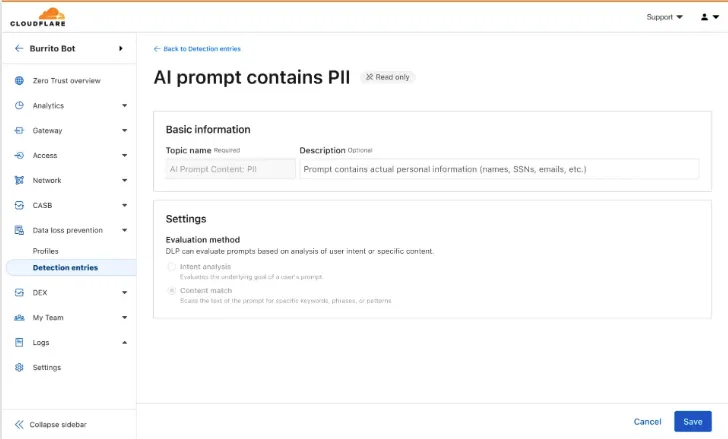
Our DLP engine performs deep analysis on each prompt, applying topic classification. These topics are grouped into two evaluation categories:
-
Content: PII, Source Code, Credentials and Secrets, Financial Information, and Customer Data.
-
Intent: Jailbreak attempts, requests for malicious code, or attempts to extract PII.
To help you apply these topics quickly, we have also released five new predefined profiles (for example, AI Prompt: AI Security, AI Prompt: PII) that bundle these new topics.
-
Granular Guardrails
You can now build guardrails using Gateway HTTP policies with application granular controls. Apply a DLP profile containing an AI prompt topic detection to individual AI applications (for example,
ChatGPT) and specific user actions (for example,SendPrompt) to block sensitive prompts.
-
Full Prompt Logging
To aid in incident investigation, an optional setting in your Gateway policy allows you to capture prompt logs to store the full interaction of prompts that trigger a policy match. To make investigations easier, logs can be filtered by
conversation_id, allowing you to reconstruct the full context of an interaction that led to a policy violation.
AI prompt protection is now available in open beta. To learn more about it, read the blog ↗ or refer to AI prompt topics.
New detection entry type: Document Matching for DLP
You can now create document-based detection entries in DLP by uploading example documents. Cloudflare will encrypt your documents and create a unique fingerprint of the file. This fingerprint is then used to identify similar documents or snippets within your organization's traffic and stored files.

Key features and benefits:
-
Upload documents, forms, or templates: Easily upload .docx and .txt files (up to 10 MB) that contain sensitive information you want to protect.
-
Granular control with similarity percentage: Define a minimum similarity percentage (0-100%) that a document must meet to trigger a detection, reducing false positives.
-
Comprehensive coverage: Apply these document-based detection entries in:
-
Gateway policies: To inspect network traffic for sensitive documents as they are uploaded or shared.
-
CASB (Cloud Access Security Broker): To scan files stored in cloud applications for sensitive documents at rest.
-
-
Identify sensitive data: This new detection entry type is ideal for identifying sensitive data within completed forms, templates, or even small snippets of a larger document, helping you prevent data exfiltration and ensure compliance.
Once uploaded and processed, you can add this new document entry into a DLP profile and policies to enhance your data protection strategy.
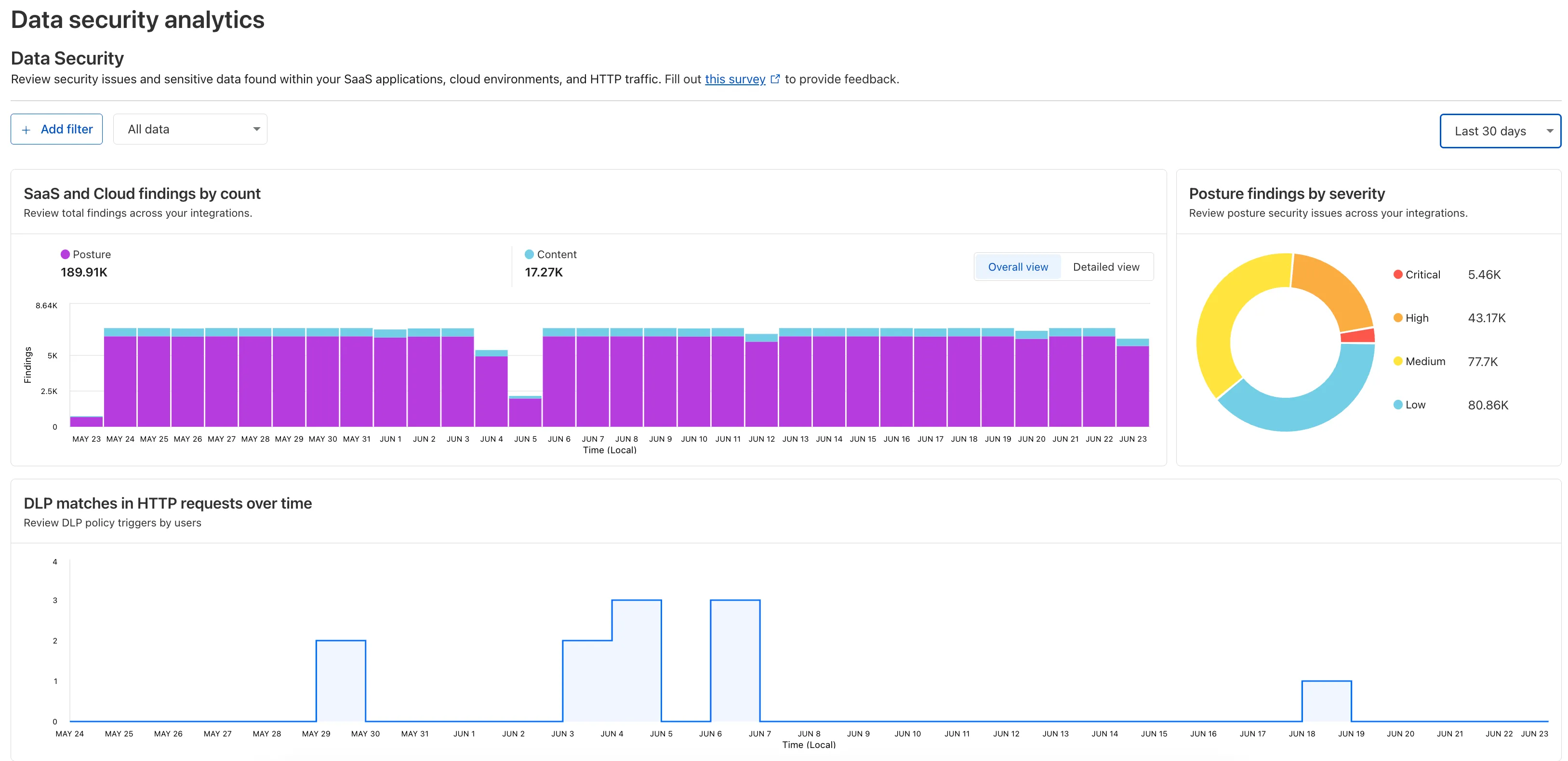
Data Security Analytics in the Zero Trust dashboard
Zero Trust now includes Data security analytics, providing you with unprecedented visibility into your organization sensitive data.
The new dashboard includes:
-
Sensitive Data Movement Over Time:
- See patterns and trends in how sensitive data moves across your environment. This helps understand where data is flowing and identify common paths.
- See patterns and trends in how sensitive data moves across your environment. This helps understand where data is flowing and identify common paths.
-
Sensitive Data at Rest in SaaS & Cloud:
- View an inventory of sensitive data stored within your corporate SaaS applications (for example, Google Drive, Microsoft 365) and cloud accounts (such as AWS S3).
-
DLP Policy Activity:
- Identify which of your Data Loss Prevention (DLP) policies are being triggered most often.
- See which specific users are responsible for triggering DLP policies.
To access the new dashboard, log in to Zero Trust ↗ and go to Analytics on the sidebar.
Case Sensitive Custom Word Lists
You can now configure custom word lists to enforce case sensitivity. This setting supports flexibility where needed and aims to reduce false positives where letter casing is critical.

Send forensic copies to storage without DLP profiles
You can now send DLP forensic copies to third-party storage for any HTTP policy with an Allow or Block action, without needing to include a DLP profile. This change increases flexibility for data handling and forensic investigation use cases.
By default, Gateway will send all matched HTTP requests to your configured DLP Forensic Copy jobs.

New predefined detection entry for ICD-11
You now have access to the World Health Organization (WHO) 2025 edition of the International Classification of Diseases 11th Revision (ICD-11) ↗ as a predefined detection entry. The new dataset can be found in the Health Information predefined profile.
ICD-10 dataset remains available for use.
Block files that are password-protected, compressed, or otherwise unscannable.
Gateway HTTP policies can now block files that are password-protected, compressed, or otherwise unscannable.
These unscannable files are now matched with the Download and Upload File Types traffic selectors for HTTP policies:
- Password-protected Microsoft Office document
- Password-protected PDF
- Password-protected ZIP archive
- Unscannable ZIP archive
To get started inspecting and modifying behavior based on these and other rules, refer to HTTP filtering.
Detect source code leaks with Data Loss Prevention
You can now detect source code leaks with Data Loss Prevention (DLP) with predefined checks against common programming languages.
The following programming languages are validated with natural language processing (NLP).
- C
- C++
- C#
- Go
- Haskell
- Java
- JavaScript
- Lua
- Python
- R
- Rust
- Swift
DLP also supports confidence level for source code profiles.
For more details, refer to DLP profiles.
Payload log match visibility
When viewing decrypted payload log matches, DLP now provides more context by listing multiple DLP matches and the matching DLP profile.
Profile confidence levels
DLP profiles now support setting a confidence level to choose how tolerant its detections are to false positives based on the context of the detection. The higher a profile's confidence level is, the less false positives will be allowed. Confidence levels include Low, Medium, or High. DLP profile confidence levels supersede context analysis.
Send entire HTTP requests to a Logpush destination
In addition to logging the payload from HTTP requests that matched a DLP policy in Cloudflare Logs, Enterprise users can now configure a Logpush job to send the entire HTTP request that triggered a DLP match to a storage destination. This allows long-term storage of full requests for use in forensic investigation.
Exact Data Match multi-entry upload support
You can now upload files with multiple columns of data as Exact Data Match datasets. DLP can use each column as a separate existing detection entry.
Data-at-rest DLP for Box and Dropbox
You can now scan your Box and Dropbox files for DLP matches.
Optical character recognition
DLP can now detect sensitive data in jpeg, jpg, and png files. This helps companies prevent the leak of sensitive data in images, such as screenshots.
Was this helpful?
- Resources
- API
- New to Cloudflare?
- Directory
- Sponsorships
- Open Source
- Support
- Help Center
- System Status
- Compliance
- GDPR
- Company
- cloudflare.com
- Our team
- Careers
- © 2025 Cloudflare, Inc.
- Privacy Policy
- Terms of Use
- Report Security Issues
- Trademark